Mimikatz is a crucial tool for conducting internal penetration tests and red team engagements due to its ability to extract passwords from memory in clear-text. Unfortunately, even adversaries have recognized its effectiveness and are using it in their operations. Despite Microsoft’s introduction of a security patch that can be applied to older operating systems like Windows 2008 Server, Mimikatz remains a potent tool that can facilitate lateral movement and domain escalation. However, it’s important to note that Mimikatz can only dump credentials and password hashes if it’s executed from the context of a privileged user, like a local administrator.
Debug Privilege
Microsoft defines the debug privilege as the permission to attach a debugger to any process or the kernel. By default, this privilege is granted to Local Administrators. However, it’s uncommon for a Local Administrator to require this privilege unless they are a system programmer.
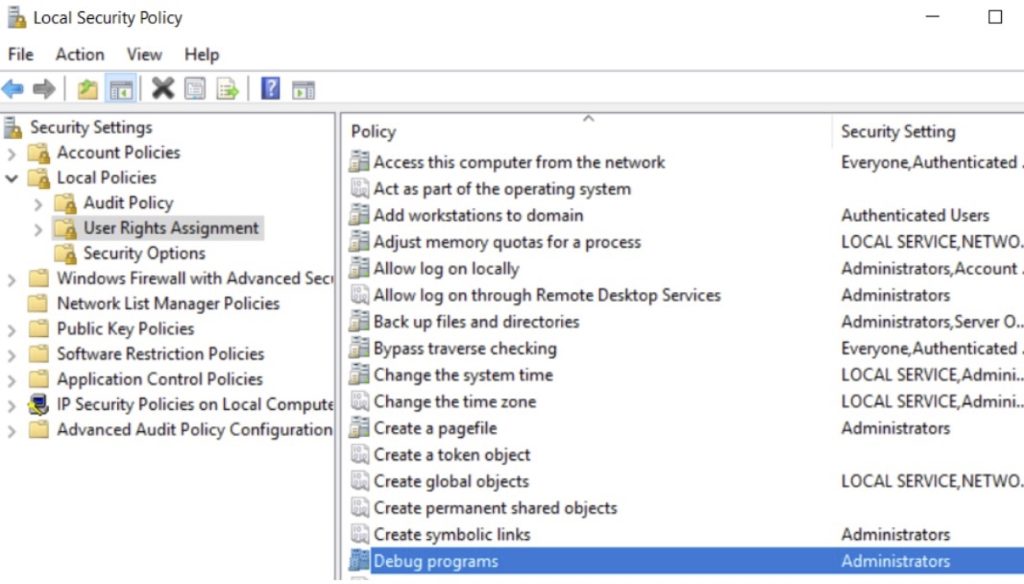
Debug programs privilege — Local Administrators
By default, in a Windows Server 2016 installation, the group policy defining the debug privilege is not enabled, meaning only Local Administrators have this permission. However, from an attacker's perspective, it's possible to check for this privilege using Mimikatz and the following command:
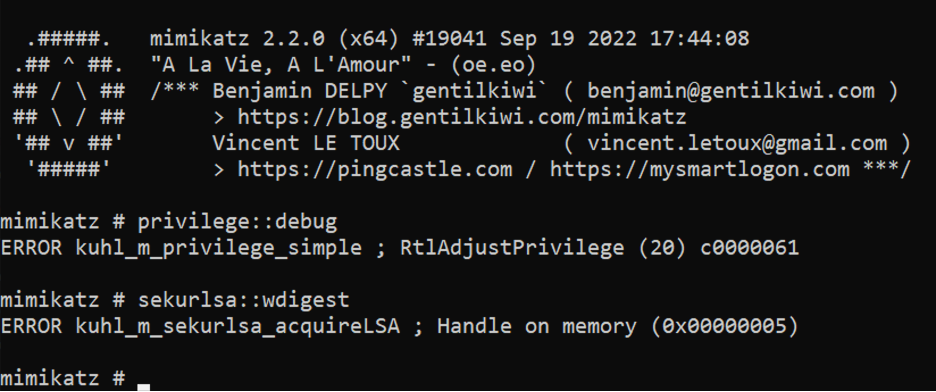
privilege::debugMimikatz needs the debug privilege to interact with processes such as LSASS. Therefore, it’s crucial to grant this privilege only to the specific group of people who require it and remove it from Local Administrators. The SeDebugPrivilege can be disabled by defining the policy with no users or groups.
Group Policy Management Editor -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment -> Debug programs -> Remove Administrators -> Apply & OK -> A restart required to apply this change.

If the new policy is applied across the domain, an attacker who has escalated their privilege to local administrator will no longer be able to use the debug privilege. Mimikatz will return the following message